In an increasingly digital economy, there is an ever-increasing threat of piracy, illegal downloads, and unauthorized streaming on unauthorized platforms. Hence, it is necessary to protect the interests of content creators and businesses - both in terms of their intellectual property rights as well as their revenue and business interests. To counter challenges posed by content pirates, forensic watermarking offers a practical solution in addition to other popular deterrents, such as the use of DRM. In this article, we’ll take a look at why forensic watermarking is important and explore types of forensic watermarking - server-side, client-side, and A/B switching-based watermarking.
What is Forensic Watermarking?
Forensic watermarking, also known as digital watermarking, is the process of embedding an imperceptible sequence of code or information directly into the video content.
This mark, embedded at random locations in the video serves as a unique identifier, allowing the content to be tracked and identified if it is copied or distributed without proper authorization.
There are several ways of inserting watermarks such as server-side watermarking, client-side watermarking, and A/B switching watermarking.
Before we study these techniques in detail, let’s look at the forensic watermarking requirements put forth by MovieLabs, a non-profit joint venture founded by the major Hollywood studios -
- The system shall have the ability to securely forensically mark video at the server and/or client to recover information necessary to address breaches.
- The watermarking shall be robust against the corruption of the forensic information.
- The watermark shall be inserted on the server or on the client such that valid insertion is guaranteed during playback even if the device and its secrets are compromised.
As you can see, forensic watermarking techniques are expected to be robust and expected to provide the ability to identify who illegally downloaded or streamed a piece of content.
Why do we need Forensic Watermarking?
Unauthorized sharing and distribution of copyrighted material not only result in financial losses but also undermine the integrity and exclusivity of intellectual property.
Content providers can employ various techniques, such as digital rights management (DRM), or secure playback environments, to enhance content protection and prevent illegal downloads or restreams of their content.
However, by embedding unique and imperceptible watermarks (forensic watermarks) directly into the video stream, content owners gain the ability to trace the origin of unauthorized copies. This allows content owners to trace the source of unauthorized copies and identify the individuals or platforms responsible. Legal action can then be taken against them.
The embedded watermark acts as a digital fingerprint, providing solid evidence of ownership and unauthorized distribution. This strengthens the legal case for content owners seeking remedies and supports their efforts in fighting copyright infringement.
Forensic watermarking plays an important role in enhancing content protection measures. It serves not only as a powerful deterrent but also as tangible evidence of ownership and unauthorized distribution, reinforcing the legal framework in the battle against copyright infringement.
Ultimately, it contributes to maintaining a secure and trusted video streaming ecosystem that benefits content creators, businesses, and consumers alike.
In the next few sections, we’ll study various watermarking techniques in detail and understand their pros, cons, and where they can be used.
Types of Watermarking Used in Video Streaming
There are many types of forensic watermarking used in video streaming and delivery.
In this article, we’ll talk about three of them - server-side watermarking, client-side watermarking, and A/B Switching watermarking.
Let’s start with server-side watermarking.
Server-Side Watermarking
Server-side forensic watermarking involves the insertion of a unique and imperceptible identifier into a single pixel of a video frame. As its name suggests, the insertion is done at the server before the video reaches the end user.
However, the goal of forensic watermarking goes beyond protecting a single frame. It aims to identify offenders involved in content leakage or piracy.
Therefore, server-side watermarking inserts the identifier at specific intervals throughout multiple frames - ensuring that the insertion pattern is unique to every streamer or audience member.
Thanks to the individualized insertion process, even when only a small segment of pirated material is discovered, content owners can extract the identifying payload from the watermark. This enables them to trace the source of the leak and take appropriate legal action.
Nevertheless, the effectiveness of server-side watermarking comes at a cost.
Unlike other watermarking solutions like client-side watermarking, it is less scalable for large audiences. Thus, its implementation is better suited for specific use cases, such as high-value corporate and military communications, pre-release Hollywood studio content, digital dailies, screeners, and content distributed to smaller audiences of fewer than 100,000 individuals.
To ensure a high level of security, each stream generated through server-side watermarking is unique to each user and cannot be cached for delivery. This safeguards the watermark's integrity and enables individual identification of unauthorized users.
It's important to note that server-side watermarking is not suitable for live-streaming scenarios due to its reliance on precise, and individualized insertion points, and the need for offline processing to extract identifying information.
In summary, server-side watermarking provides a highly secure and accurate solution for content protection, allowing content owners to track and identify offenders involved in piracy or unauthorized distribution. With its application in specific use cases, it offers valuable protection for sensitive content distributed to smaller audiences.
Let’s turn our attention to Client-Side Watermarking next.
Client-Side Watermarking
Client-side forensic watermarking in video streaming takes a different approach to watermarking. Unlike server-side watermarking, client-side watermarking is typically implemented using a software development kit (SDK) that is integrated with the video player. The SDK embeds the watermark into the video content during playback, and it can also be used to extract the watermark for forensic analysis.
You’ve probably realized by now, that this approach allows for greater flexibility and compatibility across different platforms and devices. And, obviously, it is more scalable than server-side watermarking.
However, since the embedding occurs on the client side, the watermark can be removed or altered by individuals with technical expertise. Therefore, client-side watermarking provides a lower level of security compared to server-side watermarking and is frowned upon by Hollywood studios.
So where does client-side watermarking shine, then?
Despite offering a less-secure solution, client-side forensic watermarking excels in terms of scalability. Unlike server-side watermarking, which relies on a single server for insertion, client-side watermarking distributes the burden of insertion across playback devices. This distribution allows for easy implementation, even for large audiences, making it ideal for widespread video streaming scenarios.
Due to its scalable nature, client-side watermarking finds its applications in various use cases, including live streaming events, high-volume content distribution platforms, and scenarios where scalability is of utmost importance.
Thus, it is well-suited for use cases that require scalability but may not require the highest level of content protection.
A/B Switching Watermarking
Finally, let’s take a look at A/B switching watermarking, a unique approach to watermarking that operates at the Content Delivery Network (CDN) level.
In this technique, two variants are prepared of every video segment of the content, referred to as “A” and “B”. Here we’re referring to ABR video streaming, where a video is split into segments or chunks, each of which is a few seconds long.
When a user requests a video, the video is delivered by interlacing the two variants in a unique pattern, such that, the A-B interlaced pattern allows for the identification of the user with reasonable accuracy (around 75%) when a pirated copy is detected.
Unlike server-side watermarking, A/B switching watermarking is less secure and more susceptible to compromise. If someone can figure out a way to circumvent the patterns in which the segments are delivered, then they can hack A/B switching watermarking.
However, it offers greater scalability, making it an ideal solution for scenarios where content needs to be distributed to audiences of fewer than 500,000 users.
This is primarily because while the variant creation is done at the server, the interlacing and delivery can be handled at the CDN or Edge (which are built for scalable applications). This greatly improves the scalability of the watermarking service.
In summary, A/B Session Based Watermarking, with its A/B switching approach, offers a scalable solution for tracing unauthorized copies of high-value content.
While it may not provide the same level of security as server-side watermarking, it strikes a balance between security and scalability, making it suitable for distribution to smaller audiences.
Conclusion
In conclusion, forensic watermarking emerges as a powerful and indispensable tool in the realm of content protection and piracy prevention. With the rise of digital media and the widespread availability of streaming platforms, the need to safeguard intellectual property rights has become more critical than ever.
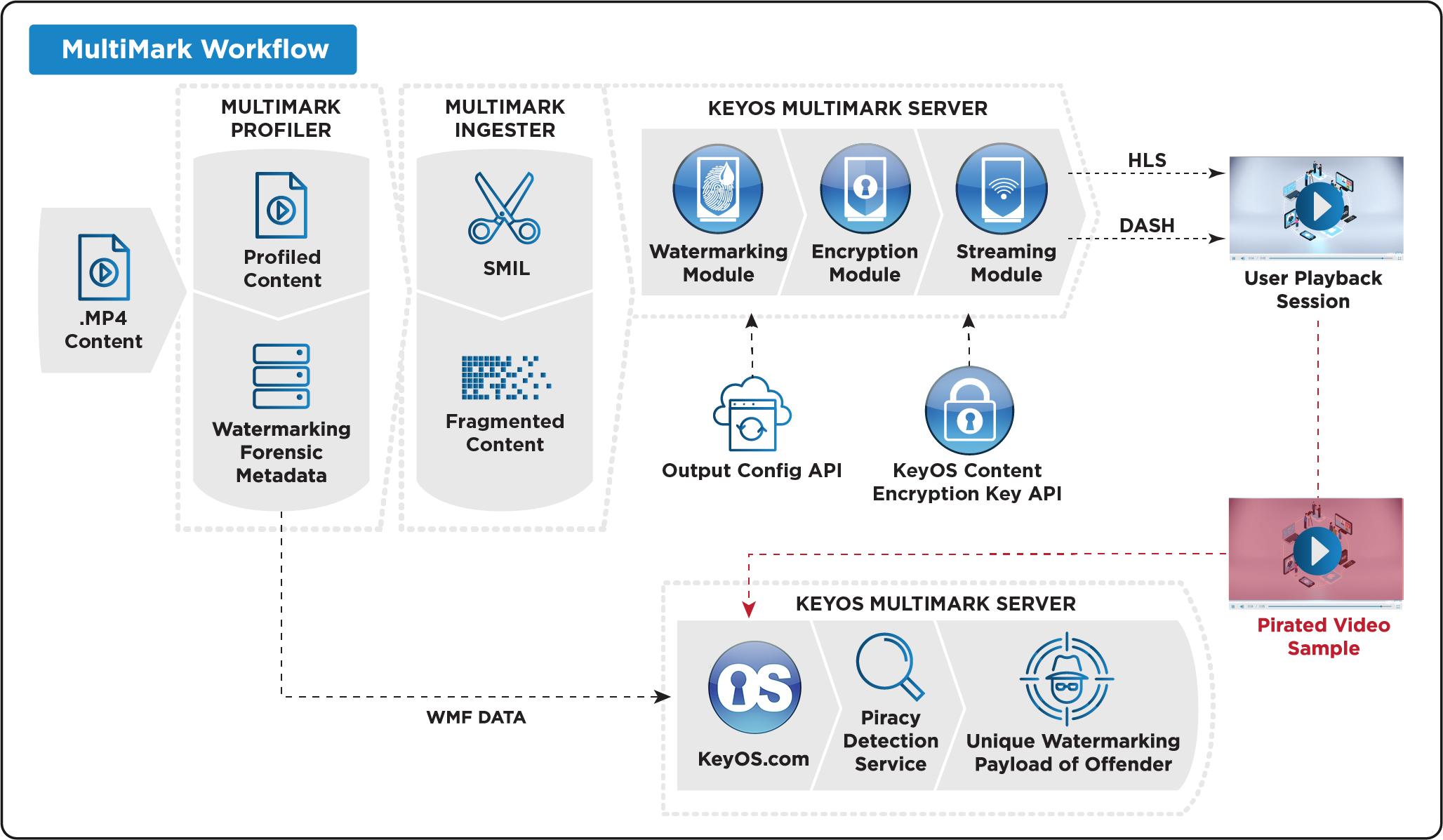
At BuyDRM, we provide state-of-the-art watermarking via our MultiMark Server platform, which is a just-in-time (JIT) forensic watermarking and DRM platform.
It enables streaming operators to watermark video content JIT and protects it with DRM before distribution. MultiMark creates and manages watermark forensic metadata (WFM) which are the unique records of all watermarking sessions. When piracy has been detected, WFM is injected into a secure detection process of the sample pirated content to track any misuse directly to the offender.
Check out our product sheet to learn more and get in touch with us for a personalized evaluation of your needs to see how we can help you.












